How are phishing attacks affecting the corporate reputation of banks?
The UK police have highlighted a number of recent scam phishing attacks in 2016 attempting to gain account log-in details and security information. Notable examples have included email-based scams targeting Ebay customers and SMS-based scams targeting Apple customers. Some involved a combination of voice and email phishing and resulted in hundreds of thousands of pounds being transferred abroad within the hour.
After it was revealed in June this year that incidents of phone fraud alone had doubled to over 11,000 in the banking sector in 2015 at a cost of £32m, alva decided to look at this issue in relation to retail banks. We analysed content relevant to Phishing (attempting to gain security information via email), Vishing (via voice or telephone) and Smishing (via SMS) with the aim of answering the following three questions:
- Are phishing attacks an increasingly visible concern for banks?
- Are vishing and smishing emerging as major threats?
- How can banks reduce the threat of phishing scams?
Is the visibility of phishing attacks increasing?
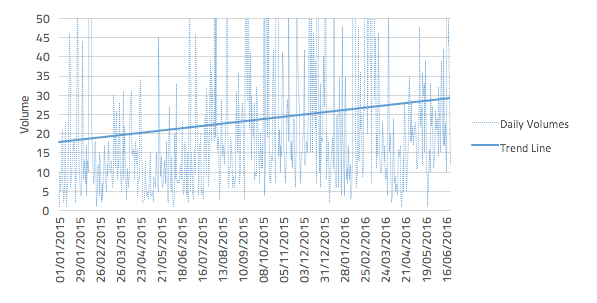
Despite significant volatility in the daily volumes of phishing, vishing and smishing content, the trend line in Figure I shows a clear upwards trend in the visibility of this issue, with the trend line illustrating a 61% increase in daily volumes.
Fig. I: References to Phishing, Vishing and Smishing combined
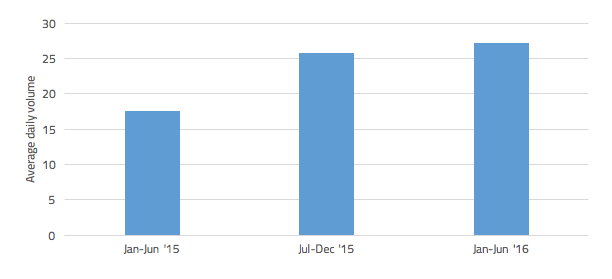
Slightly more detail emerges when looking at the average volumes in each half year period.
Fig. II: Average daily phishing attacks volumes
Figure II shows an increase in volumes each semester, with a particular jump between the first and second halves of 2015. Without an unusually high volume of relevant content in February 2015 (caused by reaction to one consumer losing £23k through SMS-based smishing), this jump would have been starker, while the second half of 2015 saw a progressive increase in volumes and visibility to a level which so far has been maintained in 2016.
The visibility of phishing, vishing and smishing combined has increased in each of the past three periods of six months. There was a particularly notable surge in the visibility of these scams in the second half of 2015 after a string of phishing attacks lead to the likes of NatWest, PayPal and the police’s Action Fraud issuing subsequent warnings to be vigilant.
Are vishing and smishing emerging as major threats?
Of the three types of “social engineering” scams studied for this piece, phishing was by far the most commonly referenced, accounting for 87% of all content and consistently eclipsing vishing and smishing in terms of visibility.
One caveat to this is that while we are analysing specific references to each, vishing and smishing are still relatively new words and regularly get conflated under the umbrella term of phishing.
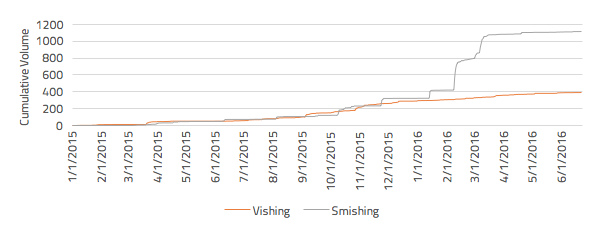
Fig. III: Cumulative Volumes of Vishing and Smishing
As Figure III shows, vishing and smishing volumes are similar throughout the majority of 2015. However, in February and March 2016, the SMS-based smishing distinguishes itself from vishing as a threat, with a clear gap emerging in the visibility of the two scams.
This difference subsequently appears to have stabilised since April, but smishing has made itself “one to watch” for signs which may imply it’s becoming a substantial threat, rather than a priority from the viewpoint of communications.
That said, the ability of smishing to gain significant coverage in a short period of time shows there is concern among the public and media. This may become amplified further as the newer terms “vishing” and “smishing” ingrain themselves further into the public lexicon.
How can banks reduce the threat of phishing scams?
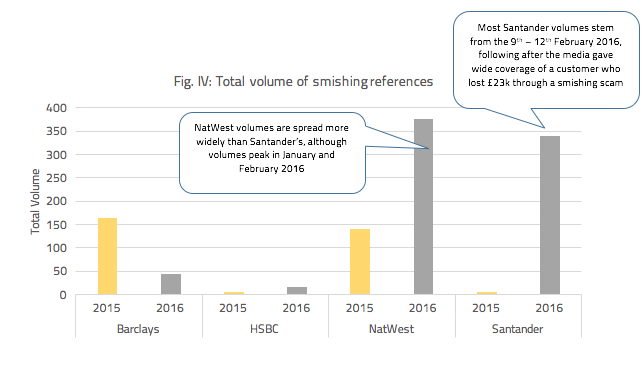
Figure IV shows the volume of content on smishing for four of the largest retail banks in the UK.
Fig. IV: Total volume of smishing references
Despite being only half way through 2016, banks have seen a significant increase in smishing related content this year, with the exception of Barclays who see a 46% pro-rata reduction.
After an apparent attempt by fraudsters to hijack the “ping-it” SMS message feed on customers’ mobiles in the latter half of 2015, the bank took action specifically aimed at reducing the risk of scams and fraud:
- In what was an “industry first”, the bank launch a TV campaign in January 2016 to raise awareness of phishing scams, in which a legitimate Barclays employee quickly calls out an impostor before offering advice. The bank plans to carry on this theme in its publicity.
- All websites are to be migrated to a .barclays or .barclaycard address, which allows the bank to control all websites using the domain (which is not the case with .com and .co.uk addresses). This increases security and trust in Barclays’ websites
As the majority of article references to phishing, vishing and smishing are negative, the reduction in 2016 of references involving Barclay’s can be seen as a success in the light of its recent actions, particularly against a backdrop in which smishing is starting to emerge as a threat in its own right.
Barclays has shown that taking visible action to raise awareness of smishing, as well as action to reduce the scope for customer error (such as placing all genuine websites inside a Barclays-controlled top-level domain name) can reduce the risk of social engineering through phishing, vishing and smishing, as well as increase trust in the organisation.
Summary
- The visibility of social engineering scams has been increased by 61% over the past 18 months.
- SMS-based smishing distinguished itself through Q1 2016 as an emerging risk above voice vishing (although email phishing is still the most visible type by a high margin), giving communicators good reason to monitor its impact. A certain “one to watch”.
- Barclays provides a potential blueprint for how communications can help reduce the risk of existing and emerging social engineering scams to the bank and its customers. Clear and public steps taken to address the issue – a public TV campaign and redefining its website addresses to increase clarity on which websites are genuine – have had a strong effect, with Barclays the only bank included in this study to see a reduction in smishing-related mentions.
Be part of the
Stakeholder Intelligence community